
In part two of the GitOps series, I will describe deploying Tandoor Recipes, an ad-free recipe application using ArgoCD and GitOps. For part 1, see GitOps Linode/OCI pt. 1.
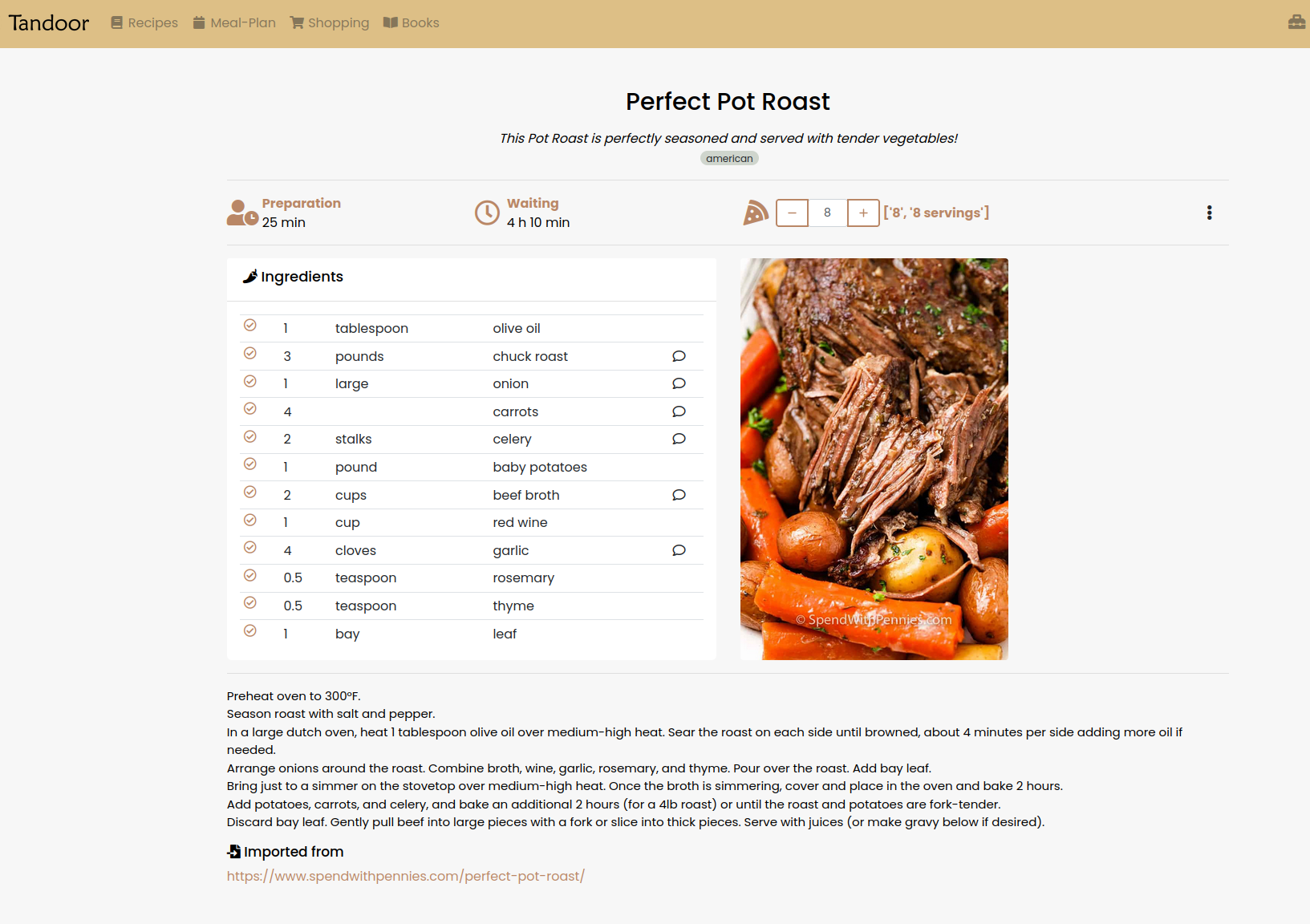
One of my biggest 2023 goals is to improve personal fitness and nutrition. Tandoor is a self-hosted meal-prepping and recipe-tracking app. Perfect for self-hosting and shaving a few pounds!
Step 4: Deploying an application
Goal: deploy Tandoor to K8s via GitOps
Tandoor does ad-free recipe importing. It removes all bloat from recipes and leaves only the recipe ingredients and steps.
Deployment steps:
- update k8s manifests
- securely store secrets
- commit manifests to Gitea
- create the application in ArgoCD UI
- Test and refine manifests until a working config
Tandoor’s Kubernetes installation docs reference a community-written manifest with all of the needed Kubernetes objects.
The only issue, the docker images used are for amd64 architecture and will not work with arm64. You’ll get an exec format error when attempting to use those.
The OCI virtual machines are arm64, meaning the manifests need to be updated with arm64 supported images.
I’ve added the updated arm64 manifests to my GitHub–> GitHub: Tandoor recipe app.
A lot of time was spent tinkering to get this working, between editing the manifests, learning the HashiCorp vault, and figuring out the Postgres stuff. I learned a lot 😄
HashiCorp Vault integration
Hashicorp Vault is an excellent way to:
Secure, store and tightly control access to tokens, passwords, certificates, and encryption keys for protecting secrets and other sensitive data using a UI, CLI, or HTTP API. - https://www.vaultproject.io/
HashiCorp Vault (HCV) is my choice for secrets management. It integrates well with k8s, and HCV replaces secret “placeholders” in YAML manifests with the vault secrets during object creation.
# Tandoor Recipes Scret with Placeholders
kind: Secret
apiVersion: v1
metadata:
name: recipes
annotations:
avp.kubernetes.io/path: "secret/data/myapp/config"
type: Opaque
data:
postgresql-password: <postgresql-password>
postgresql-postgres-password: <postgresql-postgres-password>
secret-key: <secret-key>
HCV also includes a plugin that you can set up to retrieve the secrets -> Plugin System | Vault | HashiCorp Developer
The annotation avp.kubernetes.io/path will inform the Vault plugin where the secret is stored.
The path is the location where the secret is saved in HCV.
Everything inside of <theseBrackets>is a placeholder.
What’s next?
In the next post in this series, I will dive into the CI/CD process and the solution I’ve chosen to run the pipelines.
Thanks for reading, and until next time!
Interested in learning more about GitOps/ArgoCD checkout the ArgoCD course on KodeKloud (affiliate link)
